Your backup environment is an essential resource requiring protection against unauthorized access by bad actors. You must be confident in your backups’ availability and integrity when faced with an outage or data loss scenario. Corrupted or missing backups can turn an already bad situation into a disaster that your company might not recover from.
Threat actors understand the critical roll an organization’s backups play in defending themselves against ransomware, malware, and data loss. Without valid backups, it may be impossible for a company to perform a timely recovery to address a ransomware attack. The absence of viable backups may force decision-makers to pay the ransom demands to restore access to their data resources.
Multiple measures can be utilized to protect a backup environment and minimize the threat of bad actors compromising a company’s recovery capabilities. Adopting these measures can be instrumental in maintaining the availability of consistent backups and keeping your business running when faced with unexpected outages or data loss.
Protective Measures to Safeguard Your Backup Environment
Each of the following measures increases the safety of your backup environment. Implementing multiple initiatives is recommended to bolster the protection as high as possible.
- Enforcing mandatory multi-factor authentication (MFA) – Companies should implement MFA to access the backup environment. MFA reduces the possibility of bad actors accessing your backups via compromised login credentials. Authorized users must prove their identity using multiple processes, making it much more difficult for hackers to impact the backup environment. Ideally the MFA passcode should be provided by a pre-approved application or in-house webpage and not be sent to a cellphone, as those are vulnerable to both SIM card cloning as well as social engineering.
- Enabling single sign-on (SSO) – Single sign-on consolidates account management, making it easier to ensure all accounts conform to company security policies. Centralized administration allows an organization to control access to specific resources tightly while minimizing complexity for the user base.
- Restricting the use of admin accounts – Access to admin accounts should be minimized. These powerful accounts should not be used for daily work when possible. Instead, dedicated accounts should be created to address specific processes that may need elevated privileges but do not require the full capabilities of an admin account. This practice limits the potential damage caused by a compromised account. If possible, users should be required to “check out” the administrator password from a Password Vault – one that requires they provide a good reason to be utilizing this account instead of a separate user-specific account.
- Implementing FIPS and STIG – These two sets of standards were initially devised to protect government IT systems. FIPS concentrates on standards for protecting data through encryption, hashing, and signing. STIG focuses on configuration standards to ensure secure hardware, software, and networks. Companies can adopt these standards to strengthen security and protect the backup environment.
- Maintaining patch and update management – It is recommended that all software and hardware solutions be updated regularly and patched to address newly discovered security vulnerabilities. Special attention should be given to components of the backup environment and other infrastructure elements that interact with it. Threat actors may use known security holes to compromise enterprise backups.
- Provisioning read-only accounts whenever possible – Users should only be given the access necessary to perform their roles. In many cases, read-only permissions furnish adequate access to enterprise data. Giving users full access when not required needlessly opens the door to various insider threats.
- Creating air-gapped backup copies isolates backup data from the general IT environment. This protects the backups if bad actors compromise other elements of the infrastructure. Maintaining backup integrity is essential for an effective recovery.
- Utilizing immutable backup solutions – Immutable backup solutions ensure that backed-up data cannot be changed or deleted. VAST’s cloud backup as a service (CBaaS) offers users immutable backups to protect their data. Companies can also employ write-once-read-many (WORM) storage to safeguard the integrity of backup data.
- Analyzing security logs—System logs should be continuously analyzed to identify attempts to subvert security and gain unauthorized access to the backup environment. Teams should look for signs such as repeated failed logins, that may indicate threat actors trying to compromise the infrastructure. The organization’s security team should fully investigate suspicious activities.
- Enforcing strong password standards—All accounts should be protected by strong passwords that meet minimum length and complexity requirements. Passwords should be changed regularly according to company standards. In the next section of this article we will examine password hygiene in more detail.
The Importance of Good Password Hygiene
Practicing good password hygiene is essential when protecting valuable enterprise resources. Password hygiene entails creating, managing, and protecting strong and unique passwords to minimize the possibility they will be compromised and used by threat actors to access the backup environment.
Bad actors can use compromised passwords and unauthorized access to perform multiple destructive or damaging actions.
- Hackers can use access to your accounts as a jumping-off point to initiate attacks against critical infrastructure elements.
- Compromised accounts can be leveraged to plant malware or introduce bots to the environment.
- Bad actors can steal or destroy data, or use customer-facing website graffiti to embarrass a company.
Passwords are vulnerable to various brute force attacks that attempt to guess a user’s password. They may employ simple brute force attacks or more sophisticated techniques such as dictionary attacks, credential stuffing, or rainbow tables. The best protection against brute force attacks is to utilize long and complex passwords for your accounts.
The chart below indicates how quickly brute force attacks can compromise passwords of various lengths and complexity.
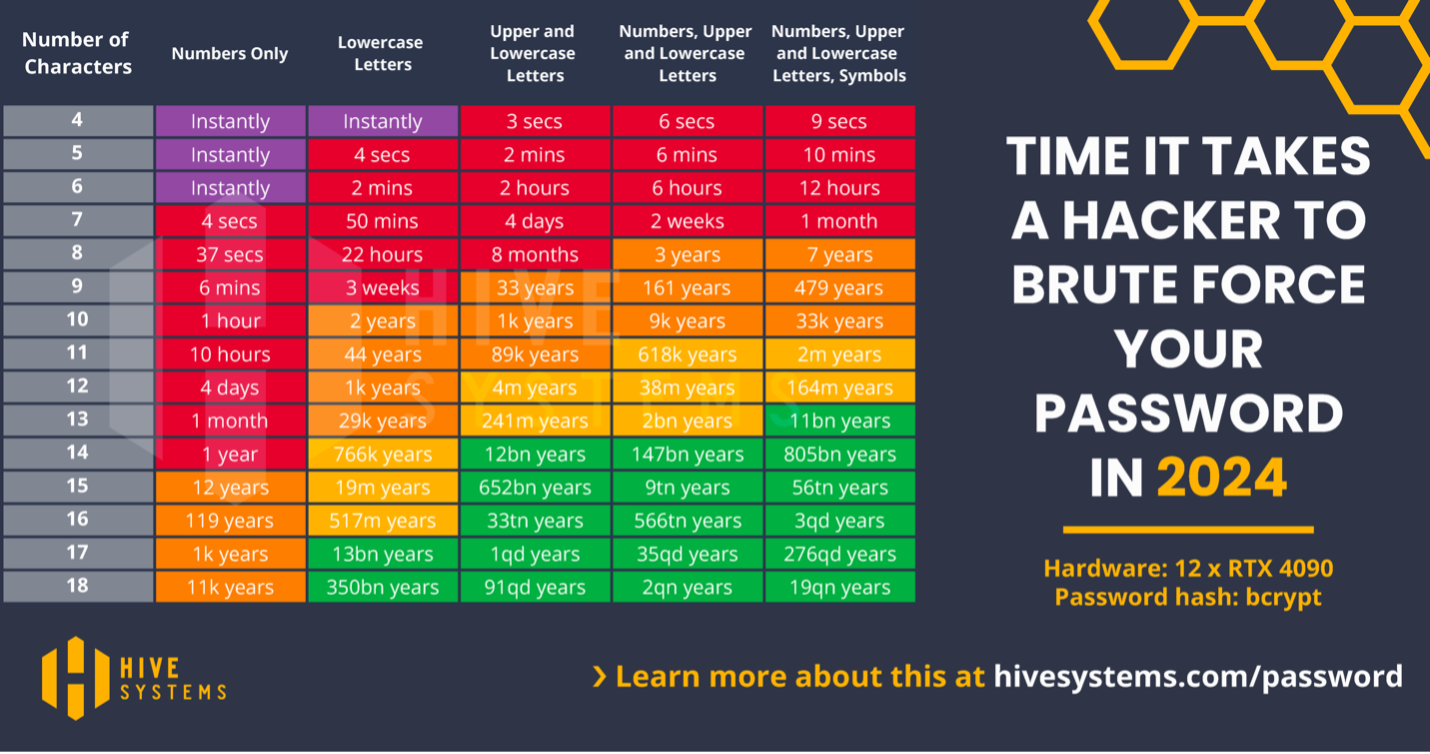
As you can see, using current technology complex passwords of more than ten characters can take thousands of years to crack. Using simple passwords just invites hackers to steal your credentials.
Advancements in computing power will undoubtedly make it easier for passwords to be cracked. Protecting your accounts without using additional tools such as a password manager may become more challenging in the years to come. A password manager simplifies using and managing long, complex, and unique passwords.
VAST’s Backup Solutions
VAST offers a CBaaS solution and other advanced backup solutions to protect your valuable enterprise data. Following the practices described above you can keep your backup environment safe and ready to recover your data. A secure backup environment can be the difference between an efficient recovery and an extended outage that puts your company at risk.
Get in touch with us and learn about how our backup offerings can protect your business.